How to Make Sure Your App Is Secure: Penetration Testing
There are many types of testing that ensure an app’s security. Whether you own a healthcare app that stores and transfers sensitive patient data or a retail app that handles users’ payment information, penetration testing might be one of the most important steps in your quality assurance strategy
In this article, we’ll talk about penetration testing, or pentesting. We’ll first define penetration testing and differentiate it from security testing, as these two types of QA activities are often confused.
What is penetration testing?
Penetration testing is analyzing a system for vulnerabilities. It’s basically an imitation of a hacker attack that shows how the system can be invaded, or penetrated. The goal of penetration testing is to find any possible deficiencies in the system’s security.
Penetration testing isn’t about virtual threats only. It also checks for any physical ways to invade the system
When a quality assurance engineer performs penetration testing, they do everything to invade databases, provoke incorrect behavior, or cause the system to shut down. Penetration testing also involves forecasting potential financial losses and economic risks. This allows developers to improve the security of a product and double-check all potential entry points.
Note that penetration testing isn’t about virtual threats only. It also checks for any physical ways to invade the system, such as through a user’s device or with physical access to the server. As a result of penetration testing, the client gets a full report that lists:
- All vulnerabilities and potential ways for a hacker to abuse the system
- The current level of security (for example, the percentage of data and code that’s encrypted)
- The time and resources needed to successfully penetrate the system
- Recommendations on removing threats and vulnerabilities
Now let’s find out what security testing is.
Security testing is the overall process of ensuring an app’s security. Penetration testing is just one part of this process. Security testing goes through all the stages of product development, from setting up the app’s architecture to testing the final version of the software. The security testing process includes:
- Risk assessment
- Scanning for vulnerabilities
- Code review and control
- Stress testing
- Penetration testing
Reasons for system vulnerabilities
Vulnerabilities can appear at any point during product development. This is why apps are regularly updated. Users who don’t update their apps regularly risk exposing their data. Let’s see what mistakes lead to vulnerabilities that penetration testing usually reveals.
- Architectural flaws are one of the most common reasons for vulnerabilities, especially in big projects that have lots of legacy code. If new features weren’t initially planned and the architecture wasn’t suitable for constant growth, the whole system will eventually become vulnerable.
- Poor connection setup. If the connection between the software and hardware is flawed, this will inevitably lead to a lack of security. This is why security issues are common for Internet of Things apps: many different devices run the same software connected by the same backend, and one unprotected request can open the door a path for hackers to all other devices.
- Weak passwords are a great way for hackers to get access to personal data. Encourage your users to come up with complex passwords and use two-factor authentication.
- Network connectivity issues. An unprotected network allows for all kinds of malware attacks, so the connection between the client and the server needs to be protected with several layers of security.
- Human error. A mistake made by an engineer or a whole team while planning, maintaining, or developing the product can result in a vulnerability.
- Complexity. This relates a bit to architectural flaws. If the system is complex, it’s much harder to define which request or flaw led to a data infringement. It’s also more difficult to support the system and not overlook a potential threat.
- Non-existent pathways. If there are pathway links that don’t exist on the server, they can open access to the parent catalog or even the root catalog of the whole file system.
- Resource conflicts. A vulnerability can occur if different processes compete for one resource – for example, two conflicting uploads compete for a single memory area.
- Lack of security expertise. This applies to both the development team and the client’s team that may be responsible for the backend or quality assurance.
Penetration testing exists to identify all these types of vulnerabilities, allowing you to find them before hackers themselves.
How to approach pentesting
There are three approaches to penetration testing:
- Manual testing
- Automatic testing
- A combination of manual and automatic testing
Let’s analyze these approaches and find out the most suitable option for every situation.
Manual pentesting
Manual penetration testing is performed by quality assurance experts. To pentest software, they use a standard procedure:
1. Data collection. This step is crucial for testing, and it can be done either manually or with the help of service tools that analyze the source code. These tools provide data on:
- Database versions
- Spreadsheet names
- Operating systems
- Third-party plugins
- Hardware
2. Risk estimation. After collecting data, the quality assurance specialist is able to identify security risks and create a plan for preventing breaches.
3. Exploitation. This step is when the tester attempts to penetrate the actual system using internal and external attacks.
External attacks simulate attacks that could occur from outside the system – for example, an attempt to get unauthorized access to the system’s functions and data that are related to client-centered apps and servers.
Internal attacks usually take place after unauthorized access has been granted. Their goal is to compromise the system from the inside.
4. Post-exploitation. This is the analysis stage, during which each attack is assessed according to its goal and its potential impact both on the system and on the business processes.
5. Reporting. The last step is making a report on how the penetration test went and how the system responded to it. This report includes all the data about the system, its current and potential vulnerabilities, and recommendations on eliminating them.
Automatic pentesting
Automatic penetration testing is faster and more effective than manual testing. It’s also easier to analyze its results, as automatic penetration testing software performs repeated programmed actions and automatically generates a report.
To perform automatic penetration testing, you don’t need a professional quality assurance engineer. Automatic pentesting is done by third-party tools. These are the most popular automated pentesting tools:
- Nmap
- Nessus
- Metasploit
- Wireshark
- W3af
- Kali Linux
- Acunetix
- Core Impact
Automatic + manual pentesting
This is the most common way to perform penetration testing, as it benefits from the advantages of both approaches and covers the software fully. It’s sometimes hard to test software with only automated testing. All products are different, and only your team’s QA specialists know your project from all angles.
Three methods for conducting penetration tests
In general, penetration tests fall into three major categories:
- Blackbox
- Whitebox
- Graybox
In a blackbox penetration test, the specialist knows about and uses only publicly available data – for example, the name of the company and a link to its website or mobile app. Blackbox testing is the closest to reality, as in most cases this is all the information hackers have access to.
Everything else – from the IP addresses the company uses to other websites and points of access to the internet – the QA specialist will need to find out themselves.
Whitebox testing is the complete opposite of blackbox. When using whitebox testing, the specialist gets all the data they could possibly want for testing, including administrative access to all the company’s servers.
This type of penetration testing allows for the broadest analysis of the software and can uncover all possible vulnerabilities – even those that only employees can accidentally or intentionally exploit.
Whitebox testing is usually faster to perform, as the specialist doesn’t need time to gather data and create a network map. The biggest advantage of the whitebox method is its full coverage of the system. The disadvantage, though, is that this method is in most cases far from reality, as hackers don’t possess all the data.
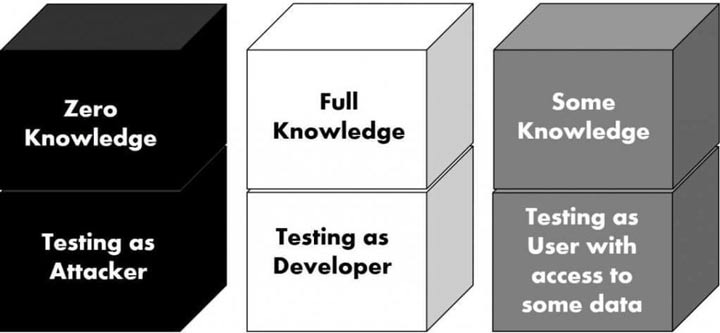
Graybox testing lies between the two extremes. In graybox testing, the specialist mostly follows the blackbox methodology, but from time to time they request additional information to reduce the time for testing. This is the most popular method, as it allows for effectively testing a system without putting in too much time and effort.
The graybox method is still rather close to a real-world situation, so its results are accurate and allow developers to protect software from external threats.
What do I get from pentesting?
As a result of pentesting, you’ll get a report that contains all the information you need to make sure your software is secure from attacks. Usually, this report contains:
- Information about the experts who created the report
- The beginning and end dates of penetration testing
- Reasons for testing
- Resources and data presented by the software owner
- Description of tools and hardware used for testing
- Description of the penetration testing process
- Description of discovered critical vulnerabilities
- Recommendations for addressing those critical vulnerabilities
Penetration testing results in a full report on all potential threats and ways to avoid them. After getting this report, you can send it to your development team so they can make sure all the risks are addressed.
After making changes to the code, you’ll need to test your software once again to make sure everything works as intended and that the security issues have been resolved.
How often do I need to pentest my software?
Hackers are evolving, and so are their tools. So pentesting your software in the beginning of the product’s lifecycle isn’t enough to ensure its security.
We recommend pentesting your software one to three times a year depending on your project
You’ll need to perform penetration testing regularly, especially if new features in your app or website involve storing and exchanging sensitive user data.
We recommend pentesting your software one to three times a year depending on your project. For healthcare, banking, insurance, or industrial software, penetration testing should happen regularly and frequently.
Wrapping up
Pentesting is an important part of security testing – probably the most important. Penetration testing allows you to see your product from a hacker’s perspective so you can find out how to keep it secure.
The best way to pentest your product is using a graybox approach, testing both automatically and manually. This will help you to get the best result in the shortest amount of time.
While security is important for all apps that have access to user data (in our world, 99% of software), penetration testing is especially necessary for any products that store and transfer health and financial data.


